Context
Deliver a fast, low-cost personal portfolio with global edge performance and strong baseline security, hosted entirely on AWS and deployed from GitHub.
Architecture
Services: S3 (static hosting), CloudFront (edge CDN), ACM (TLS), Route 53 (DNS), CloudFront Functions (redirects & security headers), optional Lambda@Edge (signed URLs for private assets).
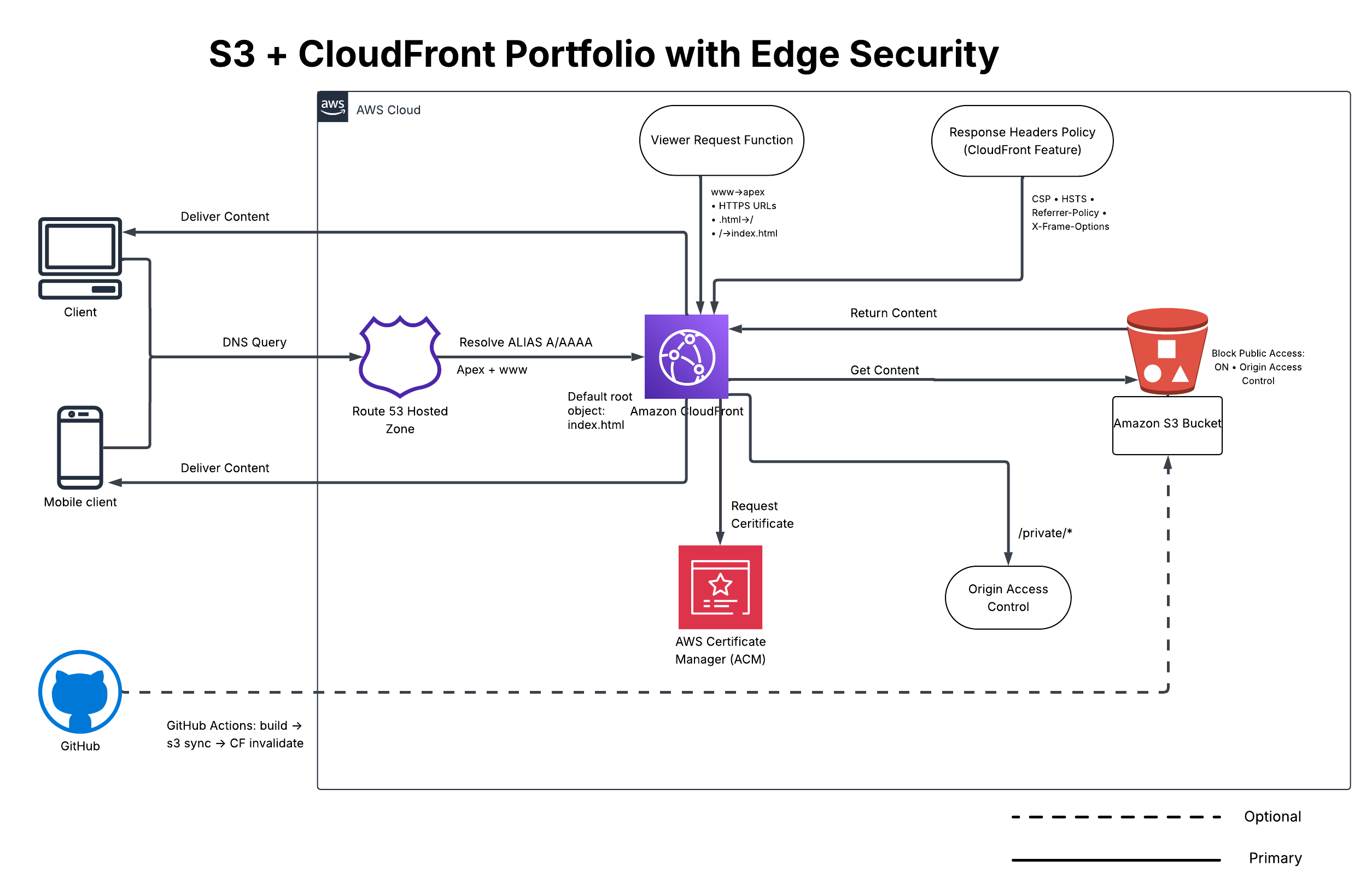
Decisions & Trade-offs
- CloudFront Functions vs Lambda@Edge: Functions are cheaper/faster for header logic; Lambda@Edge reserved for URL signing.
- Single-page then routes: Start with a single file for speed; graduate to Astro/MDX routes for scale/SEO.
- Strict CSP: Improves security; self-host fonts or allow Google Fonts domains explicitly.
Results
LCP ≤ 1.8s
INP ≤ 160ms
CLS ≤ 0.05
Cost < $1/mo*
* At portfolio traffic levels; CloudFront egress becomes the main cost at scale.
Cost & Ops
- S3 + CloudFront: pennies/month for low traffic.
- GitHub Actions: build → sync to S3 → CloudFront invalidation on merge to
main. - Observability: Plausible or CloudWatch RUM; errors in CloudFront/S3 logs.
Improvements
- Self-host fonts and tighten CSP.
- Promote to full
/projectsindex with client-side search. - Signed URLs for any private demo assets.